COVID-19 and Cyber Security Implications
Thomas Martin, Senior Lecturer, Manchester Metropolitan University
August 2020
The response to the outbreak of COVID-19 includes some of the best quality of humanity. Front-line workers are putting their lives on the line, scientists are working hard to understand and fight the virus, and the population at large are making sacrifices for the greater good. Unfortunately, it was inevitable that bad actors would look to take advantage of the situation.
It is important to try to understand how threat actors are behaving in the current environment and how they are adapting their approaches to take advantage of the lockdown in order to consider suitable countermeasures. In this article, I will examine several example attacks that have come to light and discuss their security implications.
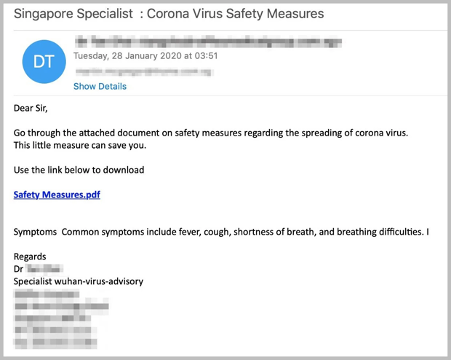
The phishers did not waste time before exploiting people’s need for information about their safety. Figure 1 shows one of the earlier examples of coronavirus-related phishing, from January 2020. What can be seen here is common to many of the examples we will review: they are trying to manipulate the target using fear. Enough fear of the consequences of this new threat (becoming infected with coronavirus) could be enough to over-ride the target’s precautions on solicited emails (not to click on links/download attachments).
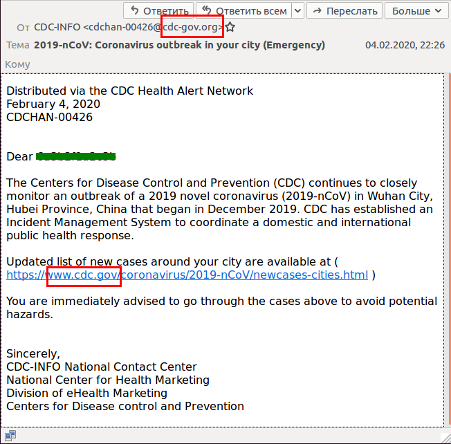
Another example is shown in Figure 2. This email is trying to take advantage of the esteem of the CDC (Centers for Disease Control and Prevention in the United States). The correct domain appears in the link and a similar looking domain in the sending email address: cdc-gov.org instead of cdc.gov. One would need to be very perceptive to notice the difference. Again, the lure is more information on the spreading disease, which would be very appealing to someone wishing to protect themselves and their loved ones. This link actually takes the target to a phishing page imitating Outlook in order to steal credentials.
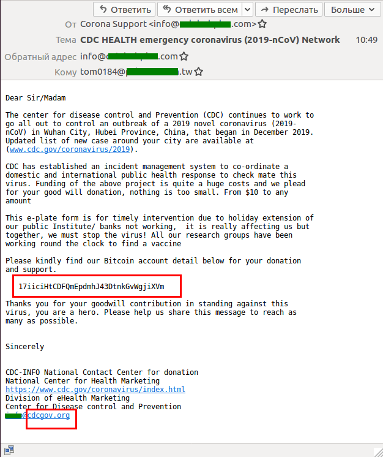
Figure 3 Image from https://www.kaspersky.com/blog/coronavirus-phishing/32395/
The example in Figure 3 again attempts to appear as coming from the CDC. The link in the body and the footer are (mostly) legitimate and the main message is asking the user to donate using Bitcoin. One giveaway is the mismatching email addresses between the “From:” address and the address in the footer. Some research on the organisation would also reveal that they do not accept Bitcoin donations, nor donations of any kind. Thanks to the transparency of the blockchain, we can see that this address has received no donations (as of 1st July 2020), but any number of wallet addresses could have been created for this particular attack.
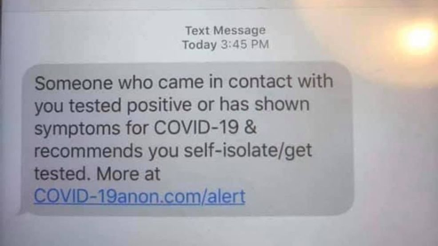
Figure 4 Image from https://security.berkeley.edu/news/scammers-are-exploiting-coronavirus-fears-phish-user
Figure 5 Image from https://security.berkeley.edu/news/scammers-are-exploiting-coronavirus-fears-phish-users
The outbreak has led to a massive numbers of scam emails attempting to exploit fears of the virus. But this is not exclusively the medium used by attackers. Figure 4 shows a text message telling the recipient that they have come into contact with someone who has COVID-19. Receiving such a text would be very disconcerting for anybody and they would be very anxious to learn more. The domain in the link provided does not relate to any long-existing and trusted organisation, but several sites have popped up recently to inform the public. The legitimate use of mass messaging/emails by governments and organisations during the pandemic can help get important information to people who need it, but also has the downside of making these fraudulent types of messages seem more trustworthy. Coupled with the increased use of track-and-trace programs, it is becoming much more difficult to tell valid messages from potential attacks.
Some of the attacks recently uncovered relied on building websites that victims would seek out, rather than directly messaging them. Figure 5 shows one such site, a map of reported outbreaks. Many people are understandably eager to know where the latest outbreaks are happening and how close they are to them and their loved ones. Malicious sites may or may not provide valid data, but their primary purpose will be to exploit vulnerabilities in the victim’s system to infect them with malware.
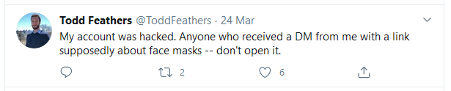
Figure 6 Taken from: https://twitter.com/ToddFeathers
Rather than trying to create a fake organisation/identity that will appear trustworthy to the target, some attackers hi-jack accounts to use the good-will and reputation that they have built up. An example of someone who suffered this directly is Todd Feathers, a tech writer who had his Twitter account taken over. The attackers posted tweets advertising a site that claimed to sell masks, as well as promoting it to his followers in DMs with the message “Masks save lives”. The task of determining who you can trust online is already a difficult one, but in light of attacks like these the question becomes two-fold:
- Do I trust this individual/organisation?
- Am I certain that they are still in control of this account?
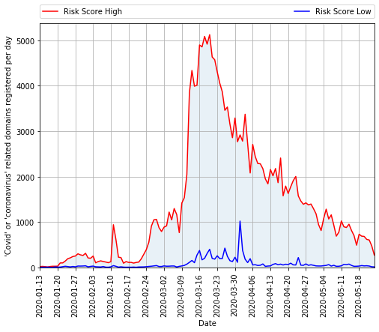
Figure 7 Image from https://www.cyberthreatcoalition.org/advisories/2020-05-26-weekly-threat-advisory
To get a sense of just how much dangerous content is out there, we can look to domain statistics. Figure 7 shows statistics on the risk level of newly registered “COVID” or “coronavirus” domains, manually assessed by the Cyber Threat Coalition. The rate at which domains are being registered and used for malicious purposes is decreasing, but there is still a vast majority of dangerous sites.
Ransomware attacks have seen no let-up in the current climate, not even for healthcare organisations. They continue to be targeted, according to a report by the Microsoft Threat Protection Intelligence Team. Read here> Access into networks is obtained through a variety of means:
- Remote desktop services using username/password authentication
- Exposed servers without security patches (either patches not applied or not available due to end-of-life)
- Misconfigured servers
Any organisation hit by a ransomware attack can find themselves with a difficult decision of having to pay a ransom (that may not result in file recovery) or restore from backup (which will cost time and effort and is likely to result in some data loss). Some branches of cyber-crime have been impacted by the lockdown. Brian Krebs wrote about the status of reshipping fraud, where stolen credit cards are used to purchase expensive items, shipped to mules, and resold. Read here>
The mules are less likely to travel to post offices or banks during the lockdown, which has impacted some of the activities. However, with many people furloughed or out of work, there are more potential mules interested in earning extra income working from home who would be willing to take the risk of receiving the goods at home.
These threats all have new elements but are fundamentally similar to attacks we have seen before. The countermeasures are largely similar to previous recommendations, but these attacks do point out specific details that should be highlighted. Email is a very common attack vector and should be treated as such. Security awareness should emphasise precaution on any email that falls outside typical patters and employees should be on the lookout for any attempts at manipulation through fear/enticement. Email is not the only problem, as just about any communication method is a potential source of misinformation or malicious intent. Everybody needs to be wary of unsolicited or unusual requests and demands. Technical measures can help deal with many of the above threats:
- Monitor for and block any malicious communications
- Apply all available updates, and migrate any systems that are past end-of-life
- Switch to two-factor authentication wherever it is supported
- Ensure that regular, reliable backups are in place and are safe from tampering
These can go someway to defending an organisation, but it takes a robust infrastructure and diligent effort by all parties to keep the shifting threats at bay.